Certificate Authority for CISA Exam - its all about trust
CISA Quick Tips 20:
CISA quick tips are published every week from Monday to Friday.Saturdays and Sundays I want them to go through my archived quick tips.Due to increase in your response and hits to my blog I thought to publish one additional article this Saturday(today).This article is very important but I have tried my best to present this in most simplified way.
I have seen many of my friends (CISA aspirants) fail to answer correctly question related to following topics:
Digital Certificate
PKI
Encryption
IPSec
SSL/TSL.
But believe me these topics are as easy as some other simple topics. To make them easily understandable i shall today present Certificate Authority in simpler form.
Before starting I recommend do not read these topics from too many sources and confuse yourself.But do not forget to read ISACA's CISA Review Manual.
When we talk about Public Key Infrastructure (PKI)/Encryption/Digital Signature, Certificate Authority (CA) plays a key role.
In today's electronic environment when information is transferred there should be a mechanism which ensures transmission to the intended recipients and recipients should be sore of the correct origin. When you do not know the intended recipient and he/she does not know you, the following questions will arise :
how to make sure of correct delivery of the message?
How to establish trust level between such source and destination?
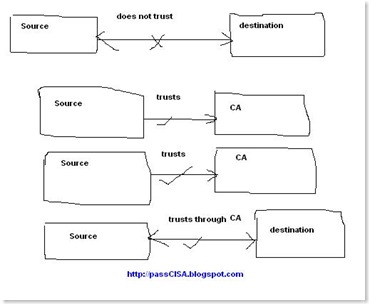
Answer is Certificate Authority (CA). How? See, the following diagram.
As source trusts Certificate Authority (CA) and the destination trusts the same Certificate Authority (CA). So both trust each other through common CA.
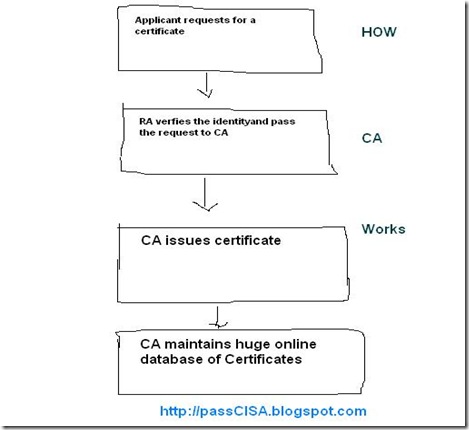
How Certificate Authority (CA) works?
Please, see the following diagram:
CA issues certificate to applicant for all verified request of Registration Authority (RA) and mantains huge database of certificates.
I believe the things are more clear to you but following Quick FAQ will clear the concept a little more.
1. What are the contents of digital certificate?
Public key
Key holder identity
Expiration date
2. What are different types of certificates?
Certificate can be of many types but important two are
Sever Certificate &
Client Certificate
3.whether all PKI will have CA?
No, but most will have.
4.When certificates can be revoked?
When keys are compromised or on expiration.
5. where expired certificate list is maitained?
in Certificate Revocation List (CRL)
6. How certificates are checked in web environment?
through web browser
CISA Type Question 20.
Which of the following is true about Certificate Authority (CA)?
1. Certificate Authority can be private for an organization
2. Certificate Authority are always commercial
3. Both A and B
4. None
Answer to CISA Type Question 19.
All of the characteristics describes Electronic Vaulting.
So, the correct answer is 2. Electronic vaulting.






10 comments:
Now i understood the concept.I referred a lot of source earlier but this topic was quite unclear.
kindly publish similar topics frequently
Jabed
i also understood
This is the way i wanted the topic.
thank you very much
Len
i also thank you for a nice post
raghav saxena.
when the sender hasing the message into a message digest or prehas code for message integrity, which is encryped using the sender's private key for authenticity, integrity and nonrepudiation. therefore, the recipient will use own public key to encrypt the message?
Yes,
I shall try to post quick tips fro the above in due course.
May I ask a question about how Digital certificates (also known as a soft token) can be used for two-factor authentication? Thanks a lot.
Thanks for writing to us. Answer to this question is being posted as a new post shortly.
Dear Angus,
Answer to your query has been posted at
http://passcisa.blogspot.com/2008/11/two-factor-authentication-using-digital_24.html
I hope this will clarify.
Thank you for a nice post and answer!
Post a Comment